
Can your business afford the following?
- Stop or delay your operations due to a cyber attack??
- Allow your information to be used by cyber criminals?
- Pay ransom to regain control of servers and computers?
- Allow your company's computer network to be infected with viruses and malware?
Above all
- Do you know what your tech system weaknesses are and how to solve them?
- Is your company updating the protections for your computer network every day?
- Does your business have the staff, time, and technology to solve these problems?
If the answer to any of the above questions is no, then your business is the right candidate for the next cyber attack.

Every day, hackers study how to violate the security of your computer systems. It is their business.
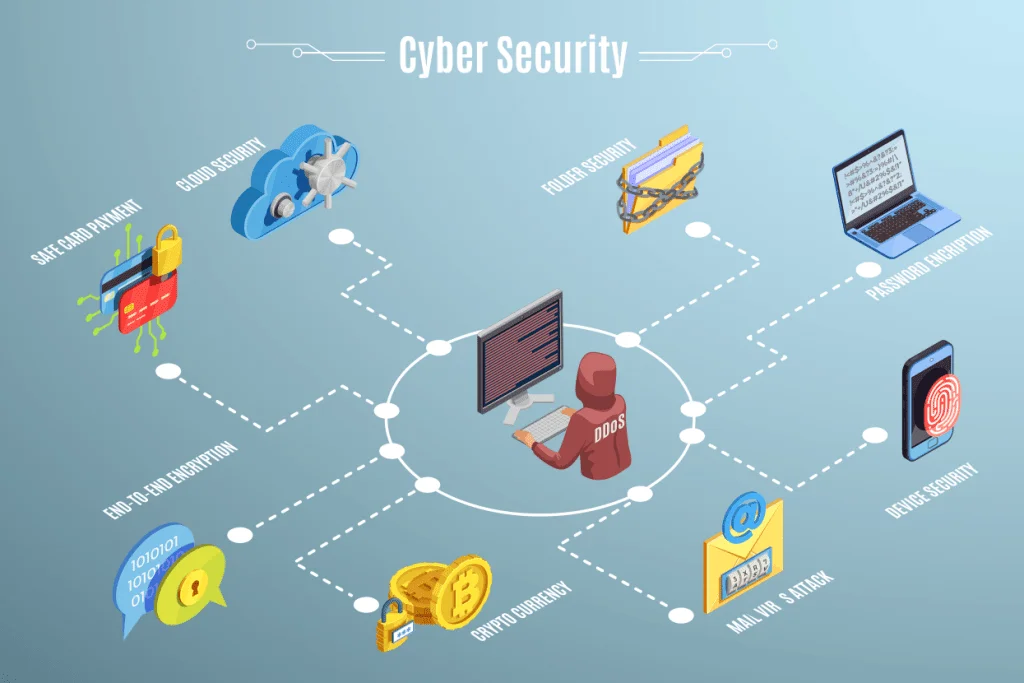
What is cyber security?
It is the protection of internet-connected systems such as hardware, software, and data from cyber threats.
Computer security
This is necessary for any business that cannot afford an interruption in its operation and crucial information loss, regardless of its size.
What is the objective of cyber security?
Provide the necessary protection for computers, servers, networks, mobile devices, and the data stored on these devices and in the cloud.
Components of cyber security
Disaster recovery
Operational security
Business continuity planning
End-user education
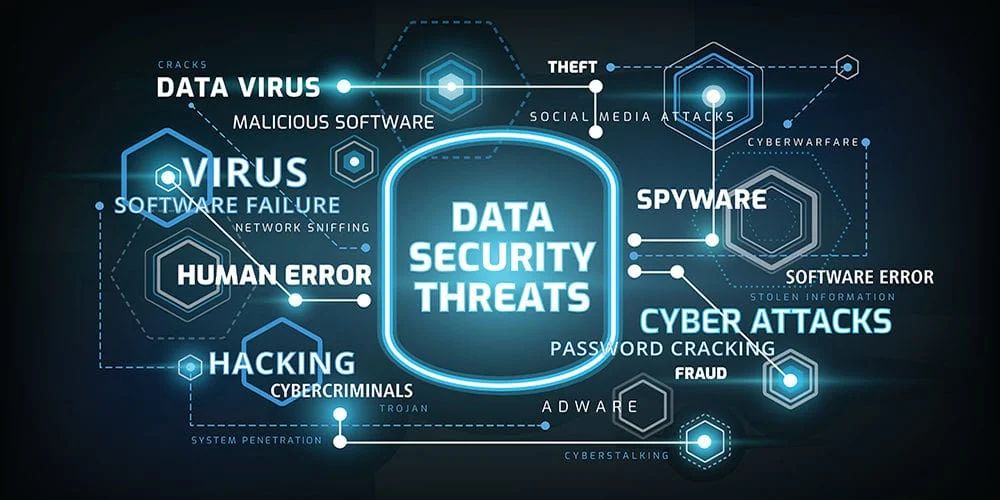
Cyber security threats
| Name | How it works | Consequence |
|---|---|---|
Ransomware |
Hackers take control of the network, computers, or databases, preventing access. | You have to pay to have the information back and access to your systems released. |
Malware |
Installation of malicious software such as worms, viruses, Trojan horses, and spyware. | Your network, computer, software, and information are damaged or altered to achieve hacker goals. |
Phishing |
Fraudulent emails looking like the ones from reputable sources are sent. | Stealing of data such as credit card, login user, passwords, and any other sensitive information. |
Social engineering |
Tactics to trick people into revealing sensitive information. | Access to confidential data, payment coercion, and malware installation. |
SQL injection |
Cyber criminals exploit vulnerabilities in data-driven applications to insert malicious code into a database. | Full access to the sensitive information contained in the database that can be stolen or altered. |
Other additional cyber threats:
- Denial-of-service attack (DoS & DDoS)
- Eavesdropping
- Multi-vector, polymorphic attacks
- Spoofing
- Tampering
The list is growing every day!
Cyber attacks and digital spying are the top threat to national security, eclipsing even terrorism.
Nothing currently indicates there'll be a decrease in cyber attacks.
Cyber security consulting
Free assessment
We perform an introductory study to evaluate what type of protection you currently have and if you have weak points in your cyber security.
Complete study
We analyze your network, pieces of equipment, risk level, compliance necessity, weaknesses, and your specific requirements to build a solution that fits your needs and budget.
Quote
We send you a complete report of our findings, analysis, and a comprehensive proposal with the reach, time frame, alternatives, and costs.
Implementation
We install all the computer security software systems and solutions agreed in our quote. We train you and your staff in the prevention and use of the solutions.
Managed Services
If your business doesn't have an IT security person, we offer you the alternative to take care of all the needs and management.
Maintenance
We take care of the updates, backups, restore, repairs, and execute the necessary activities.
It is not the question of if an attack can happen or not. It is to get prepared before it happens, and it will happen sooner or later.
Cyber security benefits
- Enjoy operations continuity and avoiding losses that affect your revenues.
- Your sensitive information will be safe, avoiding liability problems and criminal activities.
- Have peace of mind that your business will have the latest protections to prevent cyber threats.
- You will cover essential security operations functions: detection, investigation, and remediation.
- You will always have an expert by your side to carry out all the necessary procedures to guarantee your business's full operation.

Some of our partners

- It is the most complete and state of the art technological solution to protect your business against cyber attacks and other threats.
It is a global cyber security leader protecting over 500 million systems in more than 150 countries. They are used in over 38% of the world's security solutions.
Withstand advanced attacks and preserve business continuity, including Endpoint, Network, Cloud, and Human.

- Fortinet Dynamic Cloud Security Solutions provides the necessary visibility and control across cloud infrastructures, enabling secure applications and connectivity from the data center to the cloud.
Fortinet offers various web application security solutions that are ideal for cloud-based customers, improving regulatory compliance for relevant applications and API-specific security packages.
The Fortinet Security Fabric enables visibility and control that protects email messages from zero-day threats and monitors the Office 365 API layer.

- StoneFly offers High Availability (HA), a high-performance cluster, storage, backup, and disaster recovery appliances.
- Ransomware Protection Solutions
- Storage Consolidation
- Virtual Servers & Hosting
- Disaster Recovery as a Service (DRaaS)
- Managed Service Provider
- Cloud Archiving
Our tech solutions are modular and currently protecting over 500 million systems in more than 150 countries.
Frequently Asked Questions
-
Are cyber security threats increasing?
Yes, threats are increasing exponentially in sophistication, intensity, diversity, and volume. Cyber experts report significant escalation in external cyber attacks, especially from criminal organizations and foreign state-sponsored activities.
-
Do mobile devices present security risks?
Mobile devices do bring great utility in terms of convenience and allowing individuals to be "online all the time." Governments have widely deployed mobile devices for accessing resources and greater workforce productivity. However, using mobile devices to communicate and share data creates inherent security issues and adds more points of access to the network. Mobile malware threats are indeed growing, and a significant security concern with mobile devices is the device's loss.
-
What capabilities are necessary components of a cyber security strategy?
Traditional approaches focused on preventive and risk-based protective measures. Risk-based meaning that the investment in security is a function of the perceived value of the protected information. Those approaches continue to be the necessary aspects of security. However, any more state government must include two additional capabilities: vigilance and resilience.
Vigilance is continuous monitoring for threats that give early detection. Resilience is the ability to respond and recover. These capabilities must be continually enhanced to anticipate the growing threat landscape. -
How significant is privacy as a component of cyber security?
Very significant. There has been an unprecedented growth of social media, personal cloud services, and employees utilizing personal devices and third-party applications. This parallels with high profile stories on data breaches and even government accessing citizens' personal information. The issues cited by State Chief Information Security Officers include unauthorized access to personal information, compliance with state statutes on privacy, and managing information sharing with third parties.
The state government can address the leading privacy concerns by aligning operational practices with the privacy policy.
Contact Us
Location:
2200 N Commerce Pkwy., Suite 200, Weston, FL 33326
Email:
info@mobilityglobal.net
Call:
+1 954 369 2553
.png)




